A cryptographic hash function is a piece of computer code that take a piece of data and produce a (hopefully) unique short string representing it. This string will in no way resemble the input data, and you will not be able to guess the input data from it. The function always outputs the same string for the same data, and changing the data will change the output string.
For example I can use the SHA256 function on the UNIX command line to make a unique representation of my name:
# echo -n rhea | sha256sum
67f70786288b7eea9b3cf5a29e8aabd9aa623388d5fc5b5805bec8f40ee2c220 -
And if I do this again I get the same result:
# echo -n rhea | sha256sum
67f70786288b7eea9b3cf5a29e8aabd9aa623388d5fc5b5805bec8f40ee2c220 -
But if I add just one extra character I get different result:
# echo -n rheaM | sha256sum
71a9031e95fdea5b8ba187feddf8a2fc1f672c4aa59387c0274e49ce5a92a9c3 -
And importantly the amount of difference in the input has no effect on the amount of difference between the output strings:
# echo rheaN | sha256sum
ef58635bd083540e1bec82232e7104e58ccb5539166411de73d024e53d43f137 -
So the outputs of cryptographic hash functions produce identities for data that can be used to uniquely refer to the data but do not disclose the content of the data.
Hash functions achieve this by feeding the data through a complex mathematical transformation. This is a mapping through mathematical space that maintains identity and difference while occulting content.
Much like a sigil.
It’s true that if one knows the word or words abstracted to make a sigil one can recognize their traces in the sigil. But these traces are a means to an end, they are a way of producing a striking and unique new identity to focus on and invest in.
More cryptographic hash strings are created every hour than sigils have been made in the entirity of human history. Billions of mappings through mathematical platonic space to establish, conceal and communicate identity. Their consensual reality and status as exports from the platonic realm of mathematical objects make them ideal magickal material.
A full 32-byte SHA256 hash is a lot to memorize, although doing so is a feat that could be ritually powerful. It may be enough to abstract it to its first few digits, as Git commits do. We don’t need to use the hexadecimal (base-16: 0123456789ABCDEF rather than base-10: 0123456789) digit strings that are the usual human readable output of hash functions. An HTML-style colour can be represented with three or six hexidecimal digits, for example blue is 0000FF or OOF. We can choose a unique colour using the first six digits of the hash.
For example:
echo this is my intent | sha256sum
1b0fd74346abfe6858b12b8e3036649a63c09f2a049634dfe3c835f32422f58e -
As an HTML colour this is #1b0fd7:
We can also use pairs of digits as positions on a 16x16 grid, or more digits for a larger grid, or three groups of digits to produce a three dimensional path for 3D printing or importing into virtual reality.
Here’s a simple Python example:
import hashlib
digest = hashlib.sha256()
digest.update(" the spammish repetition")
digest_string = digest.hexdigest()
digest_numbers = [int(char, 16) for char in digest_string]
coords = [digest_numbers[i:i+2]
for i in range(0, len(digest_numbers), 2)]
print "%!ps\nnewpath"
print "%i %i moveto" % tuple(coords[0])
for coord in coords[1:]:
print "%s %s lineto" % tuple(coord)
print "0.25 setlinewidth\nstroke"
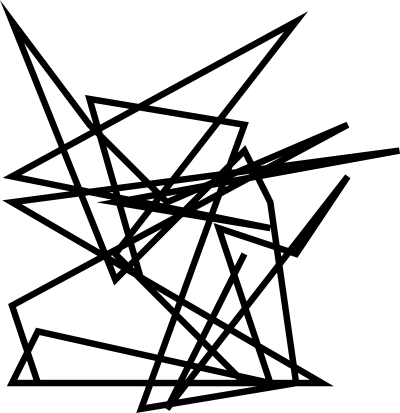
You can see the output of this program rendered at the top of this article. We can combine this with colour (or render the colours of the hash as a grid of coloured squares).
Another way of generating visual forms from hashes is using shape grammars, as used by libvisualid. Here’s “this is my intent” rendered by libvisualid:
Hashes can be attached to emails or tweets to place and circulate them in the world. Or they can be placed into the Bitcoin blockchain using a system such as https://github.com/vog/bitcoinproof, to be rehashed constantly as the Bitcoin blockchain is updated. Here’s the hash for a spell in the blockchain:
1Eui1Wje41JEJ4W1QYWbSAYG4h7JBaoPXQ
We can use a system similar to Bitcoin’s proof-of-work system to find auspicious hashes for data, those that start with a run of leading zeroes or some other number (or target string or bitmap encoded as a number).
More Python:
import hashlib
import binascii
target = "0000"
complement = -1
digest_numbers = ""
while not digest_numbers.startswith(target):
complement = complement + 1
digest = hashlib.sha256()
digest.update("this is my intent")
digest.update(str(complement))
digest_numbers = digest.hexdigest()
print "%d %s" % (complement, digest_numbers)
print binascii.b2a_uu(str(complement))
print binascii.b2a_base64(str(complement))
And its output, which is the key to creating an auspicious hash of the input string:
0 eae2ffcee00aa95306e706dd4bc67ab6b9fd2ffe61b32dfe4177b76c0afd682d
1 84ba18490876919df8bbff194eeb861c6c44a27e9bfbd8db485ecf704e41fcbd
2 f53226b118fa492dc21cd4336d67b4c8ce4148e49e8e4b094baf3e5ecff688ba
[...]
74962 38d5f823e881857f031def1822a28546d29b40903959b1c9bf1f5a1bebd42d9e
74963 b906fd259413ac714de31b9acaf6f0e5268560221d07f557f0f491a081a2cd09
74964 00006dd9f148ca454d331179bd7c87b42d7ab734df7738e1ae90e25013f02a1d
%-S0Y-C0
NzQ5NjQ=
%-S0Y-C0 and NzQ5NjQ= are different representations of the number 74964. They can be used to create sigils, or the number could be represented verbally using a mnemonic generator.
There’s more that can be done with cryptographic hashes and with cryptographic signing, which I haven’t covered in this article. But hopefully these examples can inspire further experimentation.
(All code licensed CC0.)